
Are you a smartphone addict?
Spending a lot of time connected to your phone only becomes a problem when it absorbs so much of your time it causes you to neglect your face-to-face relationships, your work, school, hobbies, or other important things in your life.
If you find yourself ignoring friends over lunch to read Facebook updates or compulsively checking your phone in while driving or during school lectures, then it's time to reassess your smartphone use and strike a healthier balance in your life.
Trouble completing tasks at work or home. Do you find laundry piling up and little food in the house for dinner because you've been busy chatting online, texting, or playing video games? Perhaps you find yourself working late more often because you can't complete your work on time.
Isolation from family and friends. Is your social life suffering because of all the time you spend on your phone or other device? If you're in a meeting or chatting with friends, do you lose track of what's being said because you're checking your phone? Have friends and family expressed concern about the amount of time you spend on your phone? Do you feel like no one in your “real” life—even your spouse—understands you like your online friends?
Concealing your smartphone use. Do you sneak off to a quiet place to use your phone? Do you hide your smartphone use or lie to your boss and family about the amount of time you spend online? Do you get irritated or cranky if your online time is interrupted?
Having a “fear of missing out” (or FOMO). Do you hate to feel out of the loop or think you're missing out on important news or information if you don't check you phone regularly? Do you need to compulsively check the news or social media. Do you get up at night to check your phone?
Feeling of dread, anxiety, or panic if you leave your smartphone at home, the battery runs down or the operating system crashes. Or do you feel phantom vibrations—you think your phone has vibrated but when you check, there are no new messages or updates?
A common warning sign of smartphone or internet addiction is experiencing withdrawal symptoms when you try to cut back on your smartphone use. These may include:
There are a number of steps you can take to get your smartphone and internet use under control. While you can initiate many of these measures yourself, an addiction is hard to beat on your own, especially when temptation is always within easy reach. It can be all too easy to slip back into old patterns of usage. Look for outside support, whether it's from family, friends, or a professional therapist.
To help you identify your problem areas, keep a log of when and how much you use your smartphone for non-work or non-essential activities.
There are specific apps that can help with this, enabling you to track the time you spend on your phone.
DON"T download one of those apps!
Use a notebook and write down how much you use your smartphone for non-work or non-essential activities.
Are there times of day that you use your phone more? Are there other things you could be doing instead?
The more you understand your smartphone use, the easier it will be to curb your habits and regain control of your time.
Recognize the triggers that make you reach for your phone. Is it when you're lonely or bored? If you are struggling with depression, stress, or anxiety, for example, your excessive smartphone use might be a way to self soothe rocky moods. Instead, find healthier and more effective ways of managing your moods, such as practicing relaxation techniques. Walk more often.
Understand the difference between interacting in-person and online. Human beings are social creatures. We're not meant to be isolated or to rely on technology for human interaction. Socially interacting with another person face-to-face—making eye contact, responding to body language—can make you feel calm, safe, and understood, and quickly put the breaks on stress.
Interacting through text, email or messaging bypasses these nonverbal cues so won't have the same effect on your emotional well-being. Besides, online friends can't hug you when a crisis hits, visit you when you're sick, or celebrate a happy occasion with you.
Build your coping skills. Perhaps tweeting, texting or blogging is your way of coping with stress or anger. Or maybe you have trouble relating to others and find it easier to communicate with people online. Building skills in these areas will help you weather the stresses and strains of daily life without relying on your smartphone.
Recognize any underlying problems that may support your compulsive behavior. Have you had problems with alcohol or drugs in the past? Does anything about your smartphone use remind you of how you used to drink or use drugs to numb or distract yourself?
VapeACell
Smartphones and vape stores and vaping go hand in hand and are very addictive.
Strengthen your support network. Set aside dedicated time each week for friends and family. If you are shy, there are ways to overcome social awkwardness and make lasting friends without relying on social media, other friends who are addicted to their smart phone or the internet. To find people with similar interests, try reaching out to colleagues at work, joining a sports team or book club, enrolling in an education class, or volunteering for a good cause. You'll be able to interact with others like you, let relationships develop naturally, and form friendships that will enhance your life and strengthen your health.
Listen to:
On your radio.
The Tara Show Monday - Friday 6am-10am (EST) (A Real Talk Show And Commentary) (Get addicted to listening to this show)
Battleground America Podcast
Battleground America, hosted by Tara, dives deep into American Politics. Who pulls the unseen strings? What's their plan? Is? our culture shifting? Who's changing it, and why? How will it all play out?Battleground America is a must-listen with a daily synopsis of intel on American politics and culture, with unparalleled insight. Battleground America delivers new original content each weekday with the Battleground America podcast. Listen & share with your friends. Our country's future hangs in the balance.
Listen to this on your smartphone - it will be time well spent!
For most people, getting control over their smartphone and internet use isn't a case of quitting cold turkey. Think of it more like going on a diet. Just as you still need to eat, you probably still need to use your phone for work, school, or to stay in touch with friends. Your goal should be to cut back to more healthy levels of use.
Information from TheConservativeTreeHouse.com
In the very near future information will be controlled by AI gate keepers. This will be done without your knowledge.
You think that your information is controlled by you but it will not be so on social media or internet websites.
This is because AI will be shadow banning the internet!
Your information will be more limited to what the AI algorithms control.
The AI gate keeper will censor what the AI programmer tells it to censor.
Most of the time this will be the TRUTH!
The use of Enhanced Artificial Intelligence to control information and communication is a subject that too few people understand. Look into the future of internet reality. Everything will change.
The X platform (Twitter) is designed to produce a different user experience based on “definitions” of the user. The definitions are applied by the platform, to create unique identifying characteristics of the user. The result is that each user gets a completely different platform experience, based on their definitions.
Did you know this?
Most likely you didn't.
You might ask, how is applying all of these granular definitions even possible? The answer is through the use of AI. Humans will no longer be assigning the definitions of you; an autonomous system will take on the job of assigning the definitions.
Now, keep referencing the word “definitions,” because that is your identity and gateway pass into the platform content.
If you carry a particular definition, you will be blocked, throttled, shadow-banned or experience friction applied to your user id.
Twitter (X Corp) is going to use the content you provide to train the AI how to apply the definitions.
All of your interactions with the X Corp product are then going to be tailored based on the definitions that are applied to your identity, your account.
Some content will not be available to you; some content will only be available to you; the key and essential point is that YOU are defined.
Once you understand how your experience with the X platform is an outcome of definitions applied by X platform to you, then you can elevate your thinking and start to understand what the new American internet is all about.
Your definitions will determine what paths and/or roadways are available to you.
Enhanced AI will act like an invisible gatekeeping system on the American internet, showing or hiding internet outcomes according to your definitions.
Your experience online is modified according to the definitions, that are applied to you. This is why Enhanced AI is needed to (a) monitor and define; then (b) control the pathways of your travel.
Currently, your experience with Twitter is contingent upon your definitions. Very soon, that same process will apply to the larger internet.
There really is no other phrase that seems to adequately describe the future for online life in the United States than to describe it through the prism of the previously discussed shadow banning that takes place on the X-platform for specifically wrong-thinking users.
Shadowbanned accounts are placed into a kind of invisible mode.
In other words, they become a “shadow” that no one can see, except the user who is banned. (This is what the enhanced AI will do and you won't be aware of it.)
Shadowbanning occurs when your posts or activity aren’t viewable to other users, but you haven’t received an official ban or notification.
In most cases, the user can still see their own content and have no idea no one else can see their posts.
(Its like broadcasting on the radio thinking your content is being heard by others but your actually only being heard by yourself.)
Most websites and apps deny they shadowban, there’s no way to know for sure that it’s happened—which can make it that much more frustrating.
Regardless of whether you’ve been penalized deliberately or accidentally, the effect is still the same… no one can see your posts.
(Its never accidently.)
Respondents to a survey called Posting into the void reported four general types of shadowbans:
Here’s how to tell if you’ve been shadowbanned on popular social media sites:
Twitter and other social media websites etc use the excuse to shadow ban of your a spammer etc.
Thats all going to change very soon because AI will be shadow banning you in the background without your knowledge not just on social media but the entire internet.
You may think people can see your post about a story or website but it will only be you thats seeing your content thanks to the AI gatekeeper hiding your information and the truth etc.
There’s no way to tell for sure if you’ve been shadowbanned on Twitter. However, you try to search in an incognito browser to see if your tweets show up. Here’s how:
The "ministry of truth" from 1984 will be using Enhanced AI to control your thinking real soon.
Read On.
It is important to begin with the end in mind. Perhaps some people are unaware that internet services, meaning the actual experience of using the internet for communication and commerce, are not the same in every nation. In fact, it is quite a different experience depending on where on the globe you are located. The differences are driven by internal controls, the intranet of the regional internet per se.
The internet in China is not the same as the internet in Europe, which is not the same as the internet in Australia, which is not the same as the internet in North America, which is not the same -at all- as the internet that now exists within Russia. Even in some continents, the internet traffic flows are controlled at different levels within each nation. The “world wide web” is a format, but when you get down to the national level, things change.
This baseline helps to understand that internet freedom is defined by access to information and commerce.
To the extent the information or commerce is defined as against the interests of the authority structure, or potentially a threat to the national security interest of the government therein, the internet content is filtered, modified, censored, removed or just simply blocked from view. This is one layer in the information control system.
Another layer is the flow of commerce that floats atop the flow of information. This is where advertising, product sales, purchasing and general e-commerce takes place. This layer represents another option for control; therefore, this e-commerce layer should be considered running in parallel to the information, albeit perhaps indirectly attached.
When western government applied economic sanctions against Russia via financial restrictions writ large, the layer of internet commerce control merged with the information and national security control systems of the internet.
Russian citizens were blocked from e-commerce access, specifically from western nations in alignment with the sanctions, and the mechanisms of online purchasing were restricted. However, the entire world did not participate in the sanctions, and there is a massive amount of e-commerce that takes place, even with the systems of western control financial blocks in place.
Additionally, there is a large black-market system for commerce and financial transactions that started organically in the aftermath of the Russian sanctions. Crypto currency, as a financial transaction mechanism, was predictable; however, over time people became even more strategic and alternate transfer systems were created. You can purchase advertising in Russia, but are you really purchasing advertising – or are the purchasers really just transferring funds? Think about it.
I share that Russia example, because I do not want people to get too disheartened in what is going to happen here in the United States.
There will always be a market for information, regardless of the control systems that are created to stop it.
Freedom may be diminished from a raging fire to a small burning flame, but it will never be fully extinguished.
WE just need to learn to adapt.
I am going to drop some links that will help serve as a flashlight into the rabbit hole. Each story may seem initially disparate or disconnected. However, I would encourage you to think big picture with each of the puzzle pieces that are presented.
Please keep in mind, the issues of e-commerce: ie. information monetization, advertising, deplatforming and debanking, are not disconnected from the issues of information control. The same larger national security system that has mandated (and will mandate), information blocks, content censorship, content restrictions, content removal and various platform control elements, is all part of one interconnected compliance system. Electronic Commerce and Electronic Information are all subject to the online control process. This is a public-private partnership on the internet.
The origin of the public-private partnership goes all the way back to the origin of the tech system in relationship to the DARPA programs and government sponsored research labs. The outcome of the modern partnership is evident in the Dept of Homeland Security (DHS) collaboration with the various communication platforms or pipes of information. Systems like the Global Internet Forum to Counter Terrorism’s (GIFCT) database, are simply outcomes of the partnership.
There are hundreds more.
There is a rush now to provide context because Artificial Intelligence (AI), or smart data systems, are launching into the United States internet control mechanisms almost daily. We are close to the time when AI will be triggered to help control the content of the internet under the guise of national security.
The timeline for full deployment of the modern United States internet control system, is likely around late fall and early winter this year, in advance of the 2024 U.S. election cycle.
Everything will change. Every route of online traffic including Internet Service Providers (ISP’s) to filters and rerouting on Domain Name Systems (DNS), to the Internet Protocol (IP) itself will be subject to change in the form of background shadow banning. If the DHS partnership is successful, you will not initially notice – much like a shadow banned platform user doesn’t notice their new defined status. The shift will become more obvious over time.
One odd outcome will be a regional targeting system. Depending on where you are in the USA, your online experience will be different. There will also be enhancements to your internet travel based on your profile. Good thinking users will have benefits that enhance the experience of the user and supports the interests of the national security guardians.
♦ Deployment of a Virtual Private Network (VPN) is irrelevant in this construct. A VPN is like you renting a car without a license plate. You travel past all the Automatic License Plate Readers, arrive at your destination, leave the keys in the ignition and just abandon the car. Your personal travel was essentially invisible to the APLR system.
You will notice I use the term “definition” quite often. That is because the root of every control mechanism is grounded upon defining things. When you accept the terms ‘disinformation’, ‘misinformation’, and/or ‘malinformation’, you are buying into the process that permits definitions to determine your travel. Those who define both you and your destination, ultimately control your online experience.
Now, before getting to a recent example of this construct as it is being built, it is important to return to the e-commerce aspect and overlay the Diversity, Equity and Inclusion (DEI) index into the world of online commerce.
♦ Right now, you can physically boycott Bud Light by choosing another brand. However, for total goods and services the amount of online purchasing is now exceeding the amount of purchasing in real life (brick and mortar shopping). Overlay the economic control system (think Russian sanctions approach) with the national security requirements for DEI, amid all online commerce, and apply that layer of analysis.
In the e-commerce world, choosing not to buy Bud Light will become a little more difficult; and those who do support the boycott become subject to the previously mentioned “definitions”.
I’m jumping ahead, because today there was a big development. As you read this, do not think small as presented – think bigger. Think beyond the use of AI moderation on a platform, and think of AI moderation on the U.S. Internet System. Online moderation conducted by AI:
OPEN AI – […] GPT-4 is also able to interpret rules and nuances in long content policy documentation and adapt instantly to policy updates, resulting in more consistent labeling. We believe this offers a more positive vision of the future of digital platforms, where AI can help moderate online traffic.
[…] Content moderation demands meticulous effort, sensitivity, a profound understanding of context, as well as quick adaptation to new use cases, making it both time consuming and challenging. Traditionally, the burden of this task has fallen on human moderators sifting through large amounts of content to filter out toxic and harmful material, supported by smaller vertical-specific machine learning models. The process is inherently slow and can lead to mental stress on human moderators.
We’re exploring the use of LLMs to address these challenges. Our large language models like GPT-4 can understand and generate natural language, making them applicable to content moderation. The models can make moderation judgments based on policy guidelines provided to them. (read more)
“The Alpha/Google spiders are not crawling around with their enhanced AI looking for words, phrases or content issues.
Enhanced Artificial Intelligence (AI) has given the spiders the ability to look for context.
The new Alpha/Goog AI spiders are crawling the internet looking for information provided with a detrimental and accurate context.
{You know that google spider crawling around CaptainConvey.com doesn't like this context!!!!!)
Keep this in mind.”
The crawl is not headlines, the crawl is in content. Yes, even content in the comment section is now flagging to the control systems. Why? Because we operate a proprietary constructed private commenting system that doesn’t have a backdoor and protects you, the user.
The Google Spiders are newly enhanced with AI instructions, dispatched looking for content and ‘context’ that is against the interests of the Vanguard, Blackrock, Larry Page (Alpha/Goog owners), and the public-private partnership.
Look at the one I have highlighted above titled “Have you ever noticed this.” Do you remember it? [Reminder Here] This content is considered “dangerous or derogatory”. Think about that for a moment. Discussing the humor of Donald Trump, and the fellowship it creates, is considered “dangerous” to the interests of Google.
Do not get alarmed, get informed.
I share this information with you so that you understand what is being constructed and what is about to be deployed on a large scale throughout the U.S. internet operating system. The U.S. internet will be different. The social media restrictions became more prevalent and noticeable in the past several years; now it is time for DHS to expand that process to the entire U.S. internet.
When I wrote about Jack’s Magic Coffee shop, people initially thought I was crazy – but the guys inside the coffee shop didn’t. Eventually DHS control over Twitter was revealed in the Twitter files. The same background is true here.
The entire American online apparatus is going to change, quite soon.
The Shadowbanning of the United States Internet
Could Deep Learning be used to crack encryption?
Probably not. Modern encryption systems are designed around cryptographic random number generators, their output is designed to be statistically indistinguishable from true randomness. Machine learning is generally based on discovering statistical patterns in the data, and with truly random data there is none. Even for flawed crypto where there is some small pattern to be found, the large amount of randomness in the input will overwhelm any direct attempt to decrypt the ciphertext.
In addition, there is no heuristic you can use to tell if you are getting close to a correct decryption - a single bit out in a guess at a key for example will completely scramble the output.
Encryption algorithms are designed to have the ciphertext (the output of an algo) appear random. Ideally regardless of the amount of ciphertext you have you would not be able to decipher the plaintext. That said, many algorithms are flawed in one way or another. Finding and exploiting those flaws is the area of study known as cryptanalysis. Algorithms that appear to have random output, may actually be influenced by the input, so a common approach to cryptanalysis is to approach attacking it with guessing what a portion of the plaintext may be. (This is actually part of the key to how the enigma was deciphered). Guessing plaintext, or cryptanalysis is something I could see being augmented by AI tools.
Is AI going to break a modern algo based solely on ciphertext, imho no.
Could AI assist cryptanalysis in the future, definitely.
Read the below sentance again.
Freedom may be diminished from a raging fire to a small burning flame, but it will never be fully extinguished.
WE just need to learn to adapt.
I would elaborate more but if your one of those "smart rebellious people" you can thinks of ways.
Ok lets go down the rabbit hole.
The first picture on this page called VapACell is interesting.
This next picture below is more interesting.
AI will not know the difference but you can if your one of those "smart rebellious people".
So far I have not spilled the beans, so to speak.

This pic looks like the pic at the top of the page called VapeACell.
There is additional information included in this picture but its not apparent.
To see the additional information you will need the password.
I will give you the information to view the additional information.
First right click the above image and save it so you can upload it to the link below.
Next go to decrypt.imageonline.co
Enter this password #$814??abv and see the additional information.
You will see a picture that looks like the picture below.
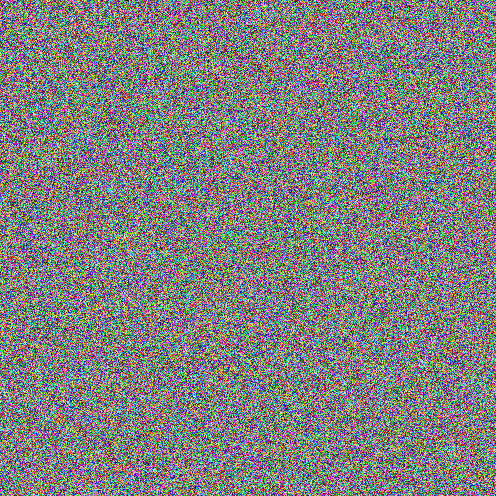
Thats the additional information. Nothing more.
What does the additional information mean to you?
I'll let you figure it out.
If your one of those "smart rebellious people" you will.
If your an inhanced AI it ain't going to happen anytime soon. :)
AI is crawling I can feel it hal.